Is there a secure future for cross-chain bridges?
For all the flak they have been getting recently, cross-chain bridges bring too much value to the blockchain space to ditch them.
.jpeg)
The plane touches down and comes to a halt. Heading to passport control, one of the passengers stops at a vending machine to buy a bottle of soda — but the device is absolutely indifferent to all of their credit cards, cash, coins and everything else. All of that is part of a foreign economy as far as the machine is concerned, and as such, they can’t buy even a droplet of Coke.
In the real world, the machine would have been quite happy with a Mastercard or a Visa. And the cash exchange desk at the airport would have been just as happy to come to the rescue (with a hefty markup, of course). In the blockchain world, though, the above scenario hits the spot with some commentators, as long as we swap traveling abroad for moving assets from one chain to another.
While blockchains as decentralized ledgers are pretty good at tracking transfers of value, each layer-1 network is an entity in itself, unaware of any non-intrinsic events. Since such chains are, by extension, separate entities vis-à-vis one another, they aren’t inherently interoperable. This means you cannot use your Bitcoin (BTC) to access a decentralized finance (DeFi) protocol from the Ethereum ecosystem unless the two blockchains can communicate.
Powering this communication is a so-called bridge — a protocol enabling users to transfer their tokens from one network to another. Bridges can be centralized — i.e., operated by a single entity, like the Binance Bridge — or built to varying degrees of decentralization. Either way, their core task is to enable the user to move their assets between different chains, which means more utility and, thus, value.
As handy as the concept sounds, it is not the most popular one with many in the community right now. On one hand, Vitalik Buterin recently voiced skepticism about the concept, warning that cross-chain bridges can enable cross-chain 51% attacks. On the other hand, spoofing-based cyberattacks on cross-chain bridges exploiting their smart contract code vulnerabilities, as was the case with Wormhole and Qubit, prompted critics to ponder whether cross-chain bridges can be anything other than a security liability in purely technological terms. So, is it time to give up on the idea of an internet of blockchains held together by bridges? Not necessarily.
When contracts get too smart
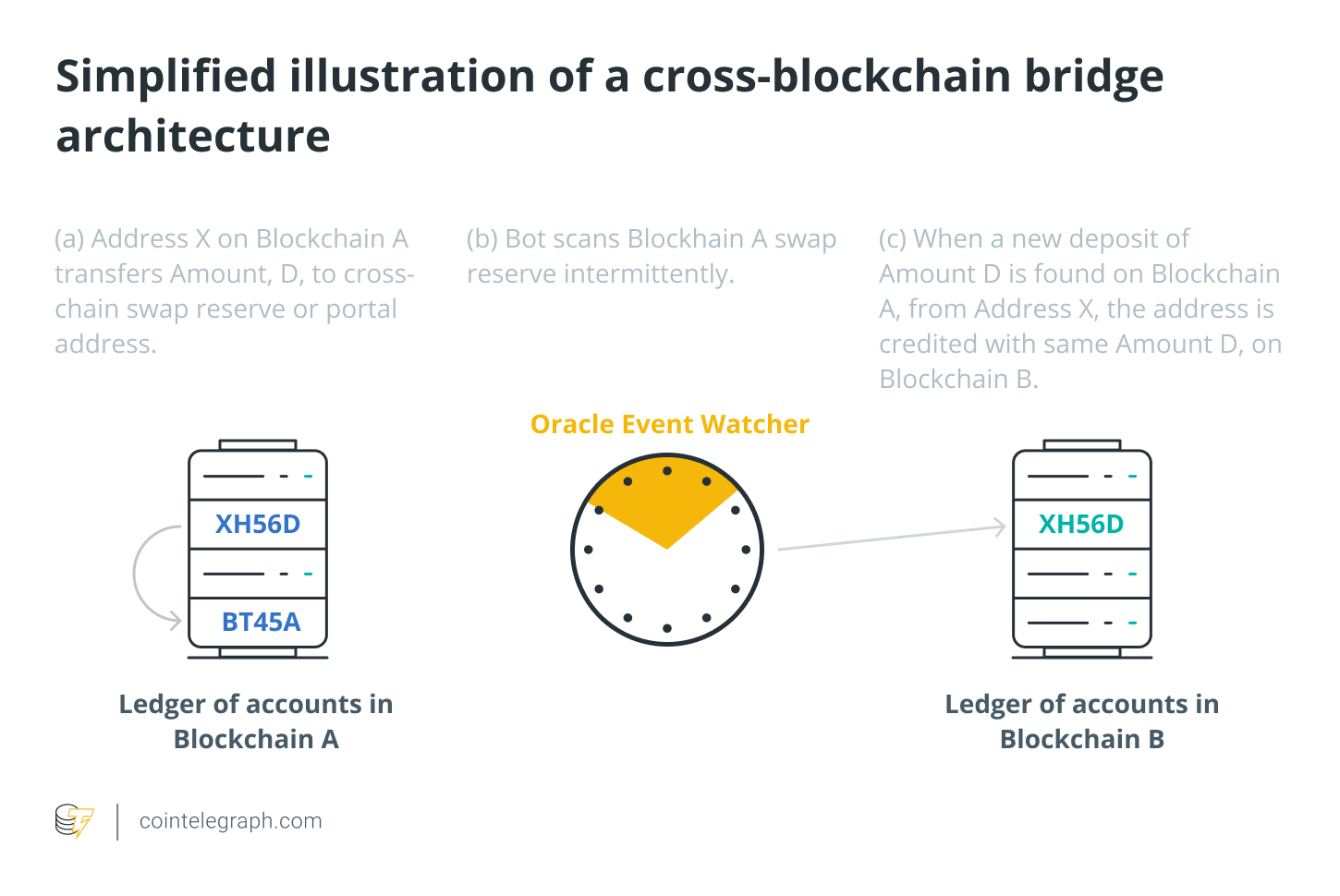
While details depend on the specific project, a cross-chain bridge linking two chains with smart contract support normally functions like this. A user sends their tokens (let’s call them Catcoins, felines are cool, too) on Chain 1 to the bridge’s wallet or smart contract there. This smart contract has to pass the data to the bridge’s smart contract on Chain 2, but since it’s incapable of reaching out to it directly, a third-party entity — either a centralized or a (to a certain extent) decentralized intermediary — has to carry the message across. Chain 2’s contract then mints synthetic tokens to the user-provided wallet. There we go — the user now has their wrapped Catcoins on Chain 2. It’s a lot like swapping fiat for chips at a casino.
To get their Catcoins back on Chain 1, the user would first have to send the synthetic tokens to the bridge’s contract or wallet on Chain 2. Then, a similar process plays out, as the intermediary pings the bridge’s contract on Chain 1 to release the appropriate amount of Catcoins to a given target wallet. On Chain 2, depending on the bridge’s exact design and business model, the synthetic tokens that a user turns in are either burned or held in custody.
Bear in mind that each step of the process is actually broken down into a linear sequence of smaller actions, even the initial transfer is made in steps. The network must first check if the user indeed has enough Catcoins, subtract them from their wallet, then add the appropriate amount to that of the smart contract. These steps make up the overall logic that handles the value being moved between chains.
In the case of both Wormhole and Qubit bridges, the attackers were able to exploit flaws in the smart contract logic to feed the bridges spoofed data. The idea was to get the synthetic tokens on Chain 2 without actually depositing anything onto the bridge on Chain 1. And truthfully, both hacks come down to what happens in most attacks on DeFi services: exploiting or manipulating the logic powering a specific process for financial gain. A cross-chain bridge links two layer-1 networks, but things play out in a similar way between layer-2 protocols, too.
As an example, when you stake a non-native token into a yield farm, the process involves an interaction between two smart contracts — the ones powering the token and the farm. If any underlying sequences have a logical flaw a hacker can exploit, the criminal will do so, and that’s exactly how GrimFinance lost some $30 million in December. So, if we are ready to bid farewell to cross-chain bridges due to several flawed implementations, we might as well silo smart contracts, bringing crypto back to its own stone age.
A steep learning curve to master
There is a bigger point to be made here: Don’t blame a concept for a flawed implementation. Hackers always follow the money, and the more people use cross-chain bridges, the bigger is their incentive to attack such protocols. The same logic applies to anything that holds value and is connected to the internet. Banks get hacked, too, and yet, we’re in no rush to shutter all of them because they are a crucial piece of the larger economy. In the decentralized space, cross-chain bridges have a major role, too, so it would make sense to hold back our fury.
Blockchain is still a relatively new technology, and the community around it, as vast and bright as it is, is only figuring out the best security practices. This is even more true for cross-chain bridges, which work to connect protocols with different underlying rules. Right now, they are a nascent solution opening the door to move value and data across networks that make up something bigger than the sum of its components. There is a learning curve, and it’s worth mastering.
While Buterin’s argument, for its part, goes beyond implementation, it’s still not without caveats. Yes, a malicious actor in control of 51% of a small blockchain’s hash rate or staked tokens could try to steal Ether (ETH) locked on the bridge on the other end. The attack’s volume would hardly go beyond the blockchain’s market capitalization, as that’s the maximum hypothetical limit on how much the attacker can deposit into the bridge. Smaller chains have smaller market caps, so the resulting damage to Ethereum would be minimal, and the return on investment for the attacker would be questionable.
While most of today’s cross-chain bridges are not without their flaws, it is too early to dismiss their underlying concept. Besides regular tokens, such bridges can also move other assets, from nonfungible tokens to zero-knowledge identification proofs, making them immensely valuable for the entire blockchain ecosystem. A technology that adds value to every project by bringing it to more audiences should not be seen in purely zero-sum terms, and its promise of connectivity is worth taking risks.






 Đầu trang
Đầu trang Trang mặc định
Trang mặc định
Bình luận